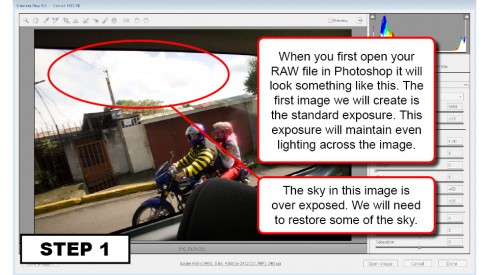
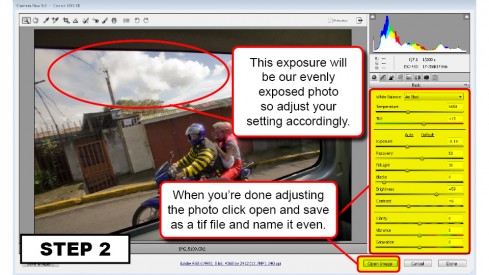
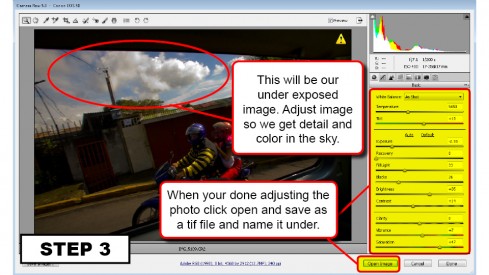
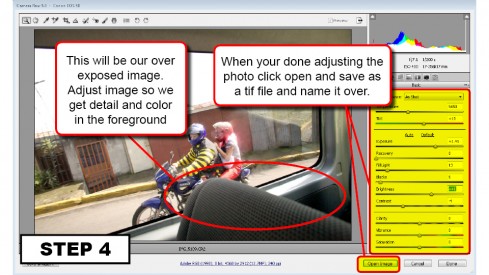
Are you new to Google+ ?
Are you a novice in Google social media?
Are you using Google+ for so many days yet unknown of it's complete features?
Do you want to be a successful Google+ user?
All these questions will be answered by this small yet monster
e-book. This is completely free of cost. Download from my Google Drive with the link provided below.
Google+ For Dummies-Free-Download
[Link Closed]
This e-book is truly portable. It is a slim volume of 146 pages. It uses the typical graphic clues and hints that have made all the Dummies guides easy to use. One important thing to note is that features may not be identical to what is talked about in the e-book. Google+ is being improved and new features are added almost every month.
This will always be the case for any e-book written about the internet, social networking, and the web. If you are new to Google+, the best way to use this e-book is to start at the beginning and follow through step by step on how to set up your account and profile.
Chapter 1 covers in clear and easy to understand instruction covering how to set up your profile, circles settings, following others, +1 stuff, and creating your first post.
One of the most powerful features of Google+ is its circles. It can also be one of the most confusing. Circles are how you organize the people you follow.
Chapter 2 provides easy to comprehend step by step instructions on using circles and setting up your privacy functions.
Google+ is meant for sharing and Chapter 3, “Posting to Google+,” is all about it. It walks you through what to post, who to post to, sharing, resharing, commenting, moderating your posts, and handling the inevitable troll, “someone who constantly criticizes just to criticize, constantly nags, and never gives up.” You will get trolls under the bridge from time to time.
One of the most popular and potentially useful features of Google+ is the Hangout. Hangout is video chat with potentially more than one person at a time. Chapter 4 gives you all the instructions you need to be successful in this. All you will have to provide is the computer with a webcam and, hopefully, witty conversation.
One feature that has great potential but is still underdeveloped is Sparks. Sparks allows you to create searches of Google that you can use and share with other in Google+. Chapter 5 covers how to pick your sparks, and how to read and interact with them.
One fun feature of Google+ is games. Chapter 6 instructs you on how to find games to play, read about what others are doing in their games (the Game Stream), and how to challenge others to games. you can even play Angry Birds within Google+ Games!
Etiquette on social networks is important. Chapter 7 provides a good background for the Google+ newbie with guidance for posting and when to comment on the posts of others and more.
Google+ is available as a mobile app for iPhones, iPads, and Android phones and tablets. The mobile apps have features not available via the web-based version of Google+. Chapter 8 discusses the apps and how to use them. You can actually find out who is “Nearby” using Google+ if you have GPS and location services activated on your mobile device. The mobile apps also have a chat feature called Huddles for group chats.
One feature that many people love is Google+ Photos. Chapter 9 tells you how to view photos taken of you, taken on your phone, and how to upload photos. It also covers tagging others in photos, privacy settings, and sharing your photos. You just provide the pictures!
One problem with many social networks is having access to your data for backing it up. Google+ allows you to do that. Chapter 10 provides step by step directions for backing it up. Try doing that with Facebook or Twitter!
You may not be happy with the “look and feel” of Google+. If you use Google Chrome, you can use third-party extensions to change or improve how Google+ looks. Chapter 11 has some suggested extensions. Some of these are not needed any more because of recent changes in Google+. I highly recommend you only use extensions for Google+ that come from the Google Chrome Store.